Enumeration
- Domain
- GPO
- ACL
- Trusts
- User Hunting
- BloodHound
Domain Enumeration:
For enumeration we can use the following tools
− The ActiveDirectory PowerShell module (MS signed and works even in PowerShell CLM)
Active Directory Administration with PowerShell
Import-Module C:\AD\Tools\ADModule-master\Microsoft.ActiveDirectory.Management.dll
Import-Module C:\AD\Tools\ADModule-master\ActiveDirectory\ActiveDirectory.psd1
BTW, we can use ipmo as an Alias for Import-Module
BloodHound (C# and PowerShell Collectors):
PowerView (PowerShell):
. C:\AD\Tools\PowerView.ps1
SharpView (C#) - Doesn’t support filtering using Pipeline:
Resources:
Deploy PowerShell ActiveDirectory Module Without Installing the Remote Server Tools
Domain Enumeration from PowerShell (CLM)
Get current domain:
Get-Domain (PowerView)
Get-ADDomain (ActiveDirectory Module)
Get object of another domain:
Get-Domain -Domain domain.local
Get-ADDomain -Identity domain.local
Get domain SID for the current domain:
Get-DomainSID
(Get-ADDomain).DomainSID
Get domain policy for the current domain:
Get-DomainPolicyData
(Get-DomainPolicyData).systemaccess
Get domain policy for another domain:
(Get-DomainPolicyData -domain domain.local).systemaccess
Get domain controllers for the current domain:
Get-DomainController
Get-ADDomainController
Get domain controllers for another domain:
Get-DomainController -Domain domain.local
Get-ADDomainController -DomainName domain.local -Discover
Get a list of users in the current domain:
Get-DomainUser
Get-DomainUser -Identity student1
Get-ADUser -Filter * -Properties *
Get-ADUser -Identity student1 -Properties *
Get list of all properties for users in the current domain:
Get-DomainUser -Identity student1 -Properties *
Get-DomainUser -Properties samaccountname,logonCount
Get-DomainUser -Properties pwdlastset
Get-ADUser -Filter * -Properties * | select -First 1 | Get-Member -MemberType *Property | select Name
Get-ADUser -Filter * -Properties * | select name,logoncount,@{expression={[datetime]::fromFileTime($_.pwdlastset )}}
Search for a particular string in a user’s attributes:
Get-DomainUser -LDAPFilter "Description=*built*" | Select name,Description
Get-ADUser -Filter 'Description -like "*built*"' -Properties Description | select name,Description
Get a list of computers in the current domain:
Get-DomainComputer | select Name,logonCount
Get-DomainComputer -OperatingSystem "*Server 2022*"
Get-DomainComputer -Ping
Get-ADComputer -Filter * | select Name
Get-ADComputer -Filter * -Properties *
Get-ADComputer -Filter 'OperatingSystem -like "*Server 2022*"' -Properties OperatingSystem | select Name,OperatingSystem
Get-ADComputer -Filter * -Properties DNSHostName | %{Test-Connection -Count 1 -ComputerName $_.DNSHostName}
Get all the groups in the current domain:
Get-DomainGroup | select Name
Get-DomainGroup -Domain <targetdomain>
Get-ADGroup -Filter * | select Name
Get-ADGroup -Filter * -Properties *
Get all groups containing the word “admin” in group name:
Get-DomainGroup *admin*
Get-ADGroup -Filter 'Name -like "*admin*"' | select Name
Get all the members of the Domain Admins group:
Get-DomainGroupMember -Identity "Domain Admins" -Recurse
Get-ADGroupMember -Identity "Domain Admins" -Recursive
Get the group membership for a user:
Get-DomainGroup -UserName "student1"
Get-ADPrincipalGroupMembership -Identity student1
List all the local groups on a machine (needs administrator privs on non-dc machines) :
Get-NetLocalGroup -ComputerName domain-dc
Get members of the local group “Administrators” on a machine (needs administrator privs on non-dc machines) :
Get-NetLocalGroupMember -ComputerName domain-dc -GroupName Administrators
Get actively logged users on a computer (needs local admin rights on the target):
Get-NetLoggedon -ComputerName domain-admin
Get locally logged users on a computer (needs remote registry on the target - started by-default on server OS):
Get-LoggedonLocal -ComputerName domain-admin
Get the last logged user on a computer (needs administrative rights and remote registry on the target):
Get-LastLoggedOn -ComputerName domain-admin
Find shares on hosts in current domain:
Invoke-ShareFinder -Verbose
Find sensitive files on computers in the domain:
Invoke-FileFinder -Verbose
Get all fileservers of the domain:
Get-NetFileServer
Learning Objective 1
Enumerate following for the dollarcorp domain:
- Users
- Computers
- Domain Administrators
- Enterprise Administrators
GPO
Get list of GPO in current domain:
Get-DomainGPO
Get-DomainGPO -ComputerIdentity domain-computer
Get GPO(s) which use Restricted Groups or groups.xml for interesting users:
Get-DomainGPOLocalGroup
Get users which are in a local group of a machine using GPO:
Get-DomainGPOComputerLocalGroupMapping -ComputerIdentity domain-computer
Get machines where the given user is member of a specific group:
Get-DomainGPOUserLocalGroupMapping -Identity user -Verbose
Get OUs in a domain:
Get-DomainOU
Get-ADOrganizationalUnit -Filter * -Properties *
Get GPO applied on an OU. Read GPOname from gplink attribute from:
Get-NetOU
Get-DomainGPO -Identity "{0D1CC23D-1F20-4EEE-AF64-D99597AE2A6E}"
Get users which are in a local group of a machine in any OU using GPO:
(Get-DomainOU).distinguishedname | %{Get-DomainComputer -SearchBase $_} | Get-DomainGPOComputerLocalGroupMapping
Get users which are in a local group of a machine in a particular OU using GPO:
(Get-DomainOU -Identity 'OU=Mgmt,DC=us,DC=techcorp,DC=local').distinguishedname | %{Get-DomainComputer -SearchBase $_} | Get-DomainGPOComputerLocalGroupMapping
There is a bug in PowerView, otherwise the below command would work:
Get-DomainGPOComputerLocalGroupMapping -OUIdentity 'OU=Mgmt,DC=us,DC=techcorp,DC=local'
Learning Objective 2
Enumerate following for the dollarcorp domain:
– List all the OUs – List all the computers in the StudentMachines OU
(Get-DomainOU -Identity StudentMachines).distinguishedname | %{Get-DomainComputer -SearchBase $_} | select name
– List the GPOs – Enumerate GPO applied on the StudentMachines OU.
ACL
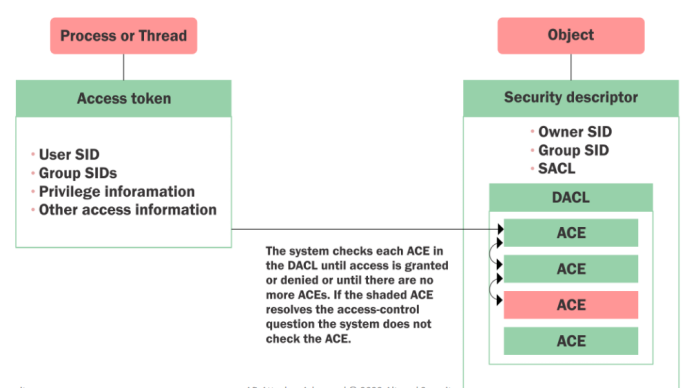
Get the ACLs associated with the specified object:
Get-DomainObjectAcl -SamAccountName student1 -ResolveGUIDs
Get the ACLs associated with the specified prefix to be used for search:
Get-DomainObjectAcl -SearchBase "LDAP://CN=DomainAdmins,CN=Users,DC=dollarcorp,DC=moneycorp,DC=local" -ResolveGUIDs -Verbose
We can also enumerate ACLs using ActiveDirectory module but without resolving GUIDs:
(Get-Acl 'AD:\CN=Administrator,CN=Users,DC=dollarcorp,DC=moneycorp,DC=local').Access
Search for interesting ACEs:
Find-InterestingDomainAcl -ResolveGUIDs
Get the ACLs associated with the specified path:
Get-PathAcl -Path "\\dcorp-dc.dollarcorp.moneycorp.local\sysvol"
Learning Objective 3
Enumerate following for the dollarcorp domain:
– ACL for the Domain Admins group – All modify rights/permissions for the studentx
Find-InterestingDomainAcl -ResolveGUIDs | ?{$_.IdentityReferenceName -match “studentx”}
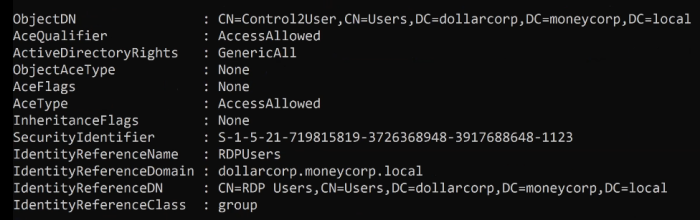
GenericAll = FullControl
reading ACL = in <ObjectDN>, (all users in) the group <IdentityReferenceName> have <ActiveDirectoryRights>
# example > in Control2User, (all users in) the group RDPUsers have GenericAll (full controll) permissions
Trusts
- In an AD environment, trust is a relationship between two domains or forests which allows users of one domain or forest to access resources in the other domain or forest.
- Trust can be automatic (parent-child, same forest etc.) or established (forest, external).
- Trusted Domain Objects (TDOs) represent the trust relationships in a domain.
Domain Trust mapping
Get a list of all domain trusts for the current domain:
Get-DomainTrust
Get-DomainTrust -Domain domain.local
Get-ADTrust
Get-ADTrust -Identity domain.local
Forest mapping
Get details about the current forest:
Get-Forest
Get-Forest -Forest domain.local
Get-ADForest
Get-ADForest -Identity domain.local
Get all domains in the current forest:
Get-ForestDomain
Get-ForestDomain -Forest domain.local
(Get-ADForest).Domains
Get all global catalogs for the current forest:
Get-ForestGlobalCatalog
Get-ForestGlobalCatalog -Forest domain.local
Get-ADForest | select -ExpandProperty GlobalCatalogs
Map trusts of a forest (no Forest trusts in the lab):
Get-ForestTrust
Get-ForestTrust -Forest domain.local
Get-ADTrust -Filter 'msDS-TrustForestTrustInfo -ne "$null"'
Learning Objective 4
- Enumerate all domains in the moneycorp.local forest.
- Map the trusts of the dollarcorp.moneycorp.local domain.
- Map External trusts in moneycorp.local forest.
Get-ForestDomain | %{Get=DomainTrust -Domain $_.Name} | ?{$_.TrustAttributes -eq “FILTER_SIDS”}
- Identify external trusts of dollarcorp domain. Can you enumerate trusts for a trusting forest?
Get-ForestDomain -Forest eurocorp.local | %{Get=DomainTrust -Domain $_.Name}
no, we cant enumerate beyong trusts relationships
User Hunting
More intrusive
Find all machines on the current domain where the current user has local admin access
Find-LocalAdminAccess -Verbose
This function queries the DC of the current or provided domain for a list of computers
(Get-NetComputer) and then use multi-threaded Invoke-CheckLocalAdminAccess on each machine.
This can also be done with the help of remote administration tools like WMI and PowerShell remoting.
Pretty useful in cases ports (RPC and SMB) used by Find-LocalAdminAccess are blocked.
See Find-WMILocalAdminAccess.ps1 and Find-PSRemotingLocalAdminAccess.ps1
Find computers where a domain admin (or specified user/group) has sessions:
Find-DomainUserLocation -Verbose
Find-DomainUserLocation -UserGroupIdentity "RDPUsers"
This function queries the DC of the current or provided domain for members of the given group (Domain Admins by default) using Get-DomainGroupMember, gets a list of computers (Get-DomainComputer) and list sessions and logged on users:
(Get-NetSession/Get-NetLoggedon) from each machine.
Note that for Server 2019 and onwards, local administrator privileges are required to list sessions.
Find computers where a domain admin session is available and current user has admin access (uses Test-AdminAccess).
Find-DomainUserLocation -CheckAccess
Find computers (File Servers and Distributed File servers) where a domainadmin session is available.
Find-DomainUserLocation -Stealth
BloodHound
can create a lot of noise
So if you can’t get caught, don’t run it. Just enumerate manually
- Provides GUI for AD entities and relationships for the data collected by its ingestors.
- Uses Graph Theory for providing the capability of mapping shortest path for interesting things like Domain Admins.
- There are built-in queries for frequently used actions.
- Also supports custom Cypher queries.
[blue team / pentester]
Supply data to BloodHound (Remember to bypass .NET AMSI):
. C:\AD\Tools\BloodHound-master\Collectors\SharpHound.ps1
Invoke-BloodHound -CollectionMethod All
or
SharpHound.exe
The generated archive can be uploaded to the BloodHound application.
[red team]
To make BloodHound collection stealthy, use Stealth option. This removes noisy collection methods like RDP, DCOM, PSRemote and LocalAdmin:
Invoke-BloodHound –Stealth
or
SharpHound.exe –-Stealth
To avoid detections like MDI:
Invoke-BloodHound -ExcludeDCs
Learning Objective 6
Setup BloodHound and identify shortest path to Domain Admins in the dollarcorp domain.
Windows outside of the domain:
runas /netonly /user:domain\user cmd.exe
sharphound-v2.0.0\SharpHound.exe -c All --domaincontroller <DC IP> --domain <domain> --ldapusername <user> --ldappassword “passwd” --distinguishedname "OU=BR"
Linux:
bloodhound-python -u <user> -p 'passwd' -ns <DC IP> -dc <FQDN> -d <domain> -c all --zip -gc <specify DC if necessary> --dns-tcp
My Mind Map
Just keep in mind that Enumeration is the MOST important part of a pentest/red team assessment
Prep Tools
inviShell
powerview
ad-module
Enum
— 1 —
Users
Computers
Domains Admins
Enterprise Admins
— 2 —
OUs
Computers in the OUs
GPOs
GPO applied to our machine
— 3 —
ACLs
All modify rights/permissions
— 4 —
All domains
Map trusts domains
Map external trusts forest
Identify external trusts. Can u enumerate?
Privesc
— 5 —
Try Local Privesc
Identify if u have local admin in other machines
Think of Estrategies
— 6 —
Setup BloodHound & identify the shortest path to DA
Getting DA
— 7 —
Identify a machine in the target domain where DA session is available
Compromise the machine and escalate to DA
— 8 —
Extract secrets from DC
Create a golden ticket with the krbtgt account secrets
Get DA with golden ticket
— 9 —
Try to get command execution on the DC by creating a Silver Ticket
— 10 —
Use DA privileges to execute Diamond Ticket
— 11 —
Use DA privileges to abuse DSRM credential for persistence
— 12 —
Check if the user has Replication (DCSync) Rights
if yes : execute DCSync to pull hashes of the krbtgt user
if no : add replication rights and execute DCSync
— 13 —
Modify Security descriptors on dc to get access using Powershell Remoting and WMI without requiring administrator access
Retrieve machine account hash from dc without using administrator access and use that to execute a Silver Ticket attack to get code execution with WMI
— 14 —
Using Kerberoasting Attack, crack password of a SQL server service account
— 15 —
Find a server in the DC where Unconstrained Delegation is enabled
Compromise the server and escalate to DA
Escalate to EA by abusing Printer Bug
— 16 —
Enumerate users in the domain for whom Contrained Delegation is enabled:
Request a TGT from the DC and obtain TGS for the service to which delegation is configured
Pass the ticket and access the service
Enumerate computer accounts for which Contrained Delegation is enabled:
For such a user, request a TGT from the DC
Obtain an alternate TGS for LDAP service on the target machine
Use the TGS for executing DCSync attack
— 17 —
Find a computer object in the domain where we have Write Permissions
Abuse the Write permissions to access that computer as DA
— 18 —
Using DA access to dollarcorp, escalate privileges to EA or DA to parent domain, moneycorp using the domain trust key
— 19 —
Using DA access to dollarcorp, escalate privileges to EA or DA to parent domain, moneycorp using dollarcorp krbtgt hash
— 20 —
With DA privileges on dollarcorp, get access to SharedWithDCorp share on the DC of eurocorp forest
— 21 —
Check if DA CS is used by the target forest and find any vulnerable/abusable templates
Abuse any such templates to escalate to DA and EA
Esc1
Esc3
Esc6
— 22 —
Get a reverse shell on a SQL Server in eurocorp forest by abusing database links from dcorp-mssql