Roadmap Pentest - 2024
A lot of people asked me (maybe 3 jk) So…
Here’s my honest opinion in what’s the most effective path to be a Pentester
There is no “correct path”. Each one build its own path, because everyone has a different background
IF you have no patience just click in the link below to go to the last chapter:

Background
So lets speak about background - What I mean by this?
“First of all Pentest is like Brazil, not for beginners” -Johnermac
- Its recommended that you have a field of expertise.
This field can vary from:
- Network Admin
- Developer
- System Admin
- Others
btw A complete beginner can start as an IT Support before choosing a more advanced field
You may ask: Why a field before pentesting is important?
Its important cause it helps you be a good professional!
“Pentest is only fun if you are good enough to find stuff”
You dont need to be an Expert in any of those, but a intermediate level gonna be helpful
How Helpful?
Pentest learns through the job, that means that u’ll Test a lot of technology that you’ve never seen before
- And if you have knowledge in those fields, u’ll mix them with the curiosity and skills of breaking stuff
Networking is gonna be helpful to understand the infrastructure, to understand the defense mechanisms in order to be stealthy and consequently bypass the defense
System admin gonna be helpful to know the commands, directories, patterns, important files, etc of a operational system (Unix, Windows, MacOS, etc)
Developer from my point of view is the most helpful field, cause you’ll be a good web pentester, you’ll learn how to develop exploits much easier and be a great asset for the team because of that
Lets say you go directly to Pentest, Its ok too, but u’ll lack fundamentals and it’ll be much harder to learn stuff on the spot
BUILD
Each professional will have these skills in rankings, just like a RPG!
Lets grab an Example:
| Network | Programming | System |
| ★★★★☆ | ★★☆☆☆ | ★★★☆☆ |
Not an Expert in any field, but have the fundamentals (or at least try to have)
This is the professional BEFORE going to PENTEST!
Besides the fundamentals, a security professional will have a large set of skills, for example:
| Fundamentals | Audit | Forensics | Reverse Engineering | Cyber Operation |
| ★★★★☆ | ★★★☆☆ | ★★☆☆☆ | ★★★☆☆ | ★★★★☆ |
There is also the SOFT SKILLS:
- Soft skills equals Communication, Documentation and Leadership
| Fundamentals | Audit | Forensics | Reverse Engineering | Cyber Operation | Soft Skills |
| ★★★★☆ | ★★★☆☆ | ★★☆☆☆ | ★★★☆☆ | ★★★★☆ | ★★★☆☆ |
And each topic has its owns sub-topics, for example:
| Web | API | Mobile | Active Directory | Container | Cloud | Physical Pentest | Low Level | etc |
Thats your BUILD. Everybody likes different things, and thats good!
Because a TEAM needs people with different set of skills and its Impossible to master everything (maybe not impossible, but lets say: it takes a lot of time )
So, As you progress you’ll have a set of skills to “build your character”
Thats why the fundamentals are important
Roadmap
Enough of Chit-Chat
OK, lets say you’re not a begginer and want to go from a Desktop Support to a Pentester (developer, network admin, sys admin is even better as I said before)
What Do I recommend?
4 Steps - straight to the point
1. Learn the fundamentals
(Basics of Security, Linux, Windows, Networking, one Programming language)
- You can learn the basics of Security from Security+ CompTIA material
- You can learn Linux from LPIC-1 LPI material or from Linux+ CompTIA material
- You can learn Network from Network+ CompTIA material
- You can learn Windows from Microsoft material
- You can learn a Programming Language with freecodecamp or CodeAcademy
- Plus - Youtube is a helpful resource for everything nowadays
The programming language can be Python, Ruby, C, C++, Javascript, C#, Java, PHP, etc doesn’t matter - pick one that you like the most
- I say that doesn’t matter, because u’ll learn others throughout your journey anyway
But if I could start again i’d choose C for internal and Javascript for external
Where to learn the fundamentals?
The best place to start in my opinion is TryHackMe. But here are some suggestions:
2. Certifications
In my opinion Certifications are important because it gives u the material organized.
btw, it can be done without certifications, but it requires a GREAT organization and patience that I dont have
Cause Sometimes you are saving money, but you are spending a lot of time to learn the same topic.
Anyway Keep in mind: Balance is everything
So, there is 2 types of certifications
- The ones that you will use to LEARN
- The ones that will help u to get a JOB
In my opinion The best PATH is
- eJPT by INE
- One full practical pentest cert (eCPPT, PNPT, CPTS) - In my opinion, the best here are the two last ones (PNPT by TCM or CPTS by HackTheBox)
- Get one cert to bypass HR + To get a JOB (OSCP, CEH) - These are the most asked, both are expensive and not great, but their purposes is to get you a job, I’d rather choose OSCP here
- After that, choose a Field of specialization (Mobile, Container, IOT, Cloud security, Car hacking, WiFi hacking, Linux, Windows, Malware Development, etc) There are so many fields, choose one that u like the most
- With XP, Certifications and a field of specialization in no time you’ll be a valuable asset for any company
3. Job = Experience
Its a bit tricky to get the first job in pentesting because everyone asks for experience, but how you are gonna get the xp in first place if nobody wanna hire you?
Nothing in this world is guaranteed, but in my point of view
If you:
- Have worked in IT before,
- Are making connections on LinkedIn (this might be the most important),
- Hold some certifications (especially OSCP),
- Showcase your projects/GitHub on your LinkedIn/Socials
You are on the right path to get a JOB in the offensive security field!
If u r feeling like you’re sending ur resume into a black hole and getting zero love in return, you’re not alone.
Perhaps you need to get a job in cyber first:
- SOC positions;
- Security Analyst;
- OSINT analyst
- etc
And then LATER switch to Pentest!
[NOTE] In your studies for Pentest, not only learn how to attack but also take some time to learn how to mitigate the vulnerability!

4. Specialization
So, you’ve nailed that job – congrats! But here’s the thing, in OffSec, the learning never stops!
Start to think which specialization u are gonna choose. And go for it.
Keep in mind that fields are inter-connected. For example:
Windows:
- If you have xp as Network Admin
- C#, Powershell, C as a language
- Active Directory
- good path for Windows specialization
Malware Developer:
- Have XP as Developer
- Enjoys low level (assembly)
- Likes to do research
- good path for maldev
WEB:
- Have IT xp
- Knows Javascript and PHP
- enjoy to do external pentesting
- can do bug bounty on free time
- good path for web
These are only examples, as I said before: u r gonna build ur own path
Anyway

What I trying to say is: U’ll get to a certain level that in order to not get stuck in ur career u gotta choose a specialization path
and every specialization has its own certifications/courses, for example:
WINDOWS:
| CRTP | CRTE | CRTO | CRTM | many others |
WEB:
| eWPT | eWPTX | OSWE | BSCP | many Others |
MOBILE:
| eMAPT | PJMT | 8kSEC | many others |
Malware Development:
| MalDev Academy | Sektor7 | OSED | many others |
Cloud:
| Altered Security | CWL | Cloud Breach | HackTricks |
First, u gotta get a job, and then u can work towards the specialization you want
- There is a lot of others certs like - SANS (expensive), EC-Council (expensive) and More
Summarizing
- Learn the Fundamentals (tryhackme/compTIA)
- Learn a programming language (Python)
- Take eJPT and PNPT
- Take OSCP (If you have enough money)
- Follow a specialization path
- Never stop learning
In this site below u can find a lot of certifications for cybersecurity in General:
Security Certification Roadmap
What certs I recommend for PENTEST:
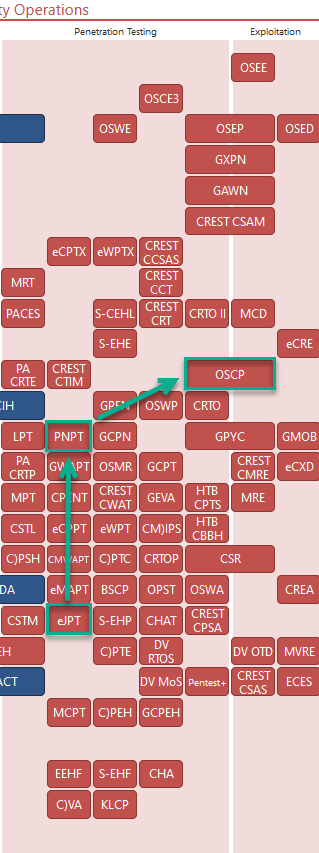
After that u can choose a specialization PATH
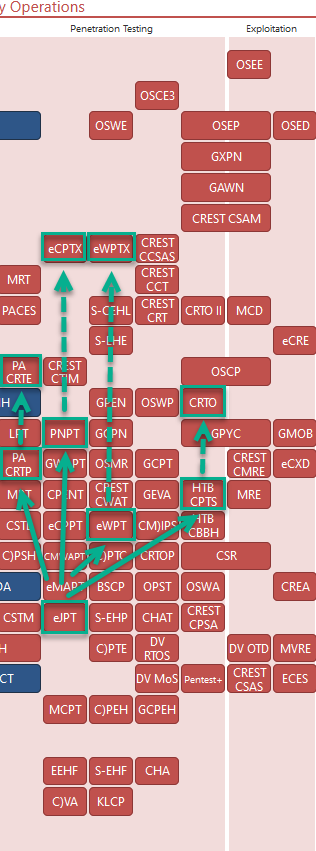
- with OSCP is easier to get a job, but lets say u dont want to spend that amount of money (like me)
Then u can think of alternatives and jump for a specialization path (AD, WEB, MOBILE, etc):
Is Pentesting Worth it?
Honestly, it’s not a paradise, but if u keep studying it can be fun
Positives:
- It can be fun
- Never stop learning mindset
- The feeling when discovering something big
- AI won’t take over (at least not yet), because manual testing yields much better results
- The possibility of becoming a criminal at any time (joking here)

Some points to consider:
- ~40% of the job is documentation
- U need to keep studying forever (it gets tiring)
- You must be at least a bit communicative, because of debriefing (its when u show the results to clients)
- Sometimes the scope of projects is just a login page of a WordPress (angry face)
- It pays well only if u are a Senior - Until there…
- It’s hard to find a job in general because the majority of the jobs are for those who know how to harden/defend systems

Expectation X Reality

| Expectation | Reality |
| It pays well | Usually pays well if u work for a bank/big company e/or u are Senior level |
| Its Fun, Its Dynamic | Its actually boring, There’s a lot of bureaucracy involved with the tests (which is part of the job) |
| You learn new stuff every day | Not every day, most likely 5% of the time |
| You are gonna hack all the time | u hack 50% of the time, 40% is documentation, 5% is debriefing and 5% is meetings |
| There’s a lack of professionals in the field | There’s a lack of SENIORS in the field |
If after reading the negative points u are still interested in the field, You’ve passed the test!
Go ahead and Good luck on ur journey!